Adopting IoT in healthcare brings remarkable benefits, but also significant security risks. Fortunately, you can manage the risks and create a secure environment for connected devices, systems, and applications by integrating DevSecOps in healthcare IoT projects.
Software companies and healthcare providers are incorporating more and more IoT devices into healthcare, including remote monitoring solutions, telehealth equipment, and more. Storing the vast amount of personally identifiable information these devices collect creates quite a few risks.
Let’s pinpoint the risks associated with healthcare-related IoT devices and software, and their implications. Next, we will explain how DevSecOps tools and practices can reinforce security during development to safeguard personally identifiable information. Finally, we’ll share the most efficient practices for implementing DevSecOps into your development pipeline and remote device network.
Security Risks of IoT in Healthcare
The more IoT device endpoints there are, the higher the risk of exposing data. The US healthcare industry faced 707 data breaches in 2022, according to the 2022 Healthcare Data Breach Report by HIPAA Journal. That number includes only the breaches involving 500 or more records. According to the report, 11 incidents each leaked over a million patient records that year.
Hackers usually get access to confidential information because of weak authentication, insufficient encryption, and careless access control, leaving data vulnerable to malicious actors. In some cases, phishing attacks exploit unaware users who follow malicious links and open infected websites.
Unsecured devices expand the attack surface
Attackers can exploit weaknesses in your IoT or IoMT (internet of medical things) software to access your databases. Unsecured remote patient monitoring devices, wearables, and mobile software can also be used as entry points to access your network. For example, a stolen portable electronic device led to the compromise of 986 patients’ information.

Data breaches can expose more patient data
The increasing volume of patient data collected by IoT devices amplifies the risks of data misuse. Without proper security considerations, users can even leak their data inadvertently by granting access rights to apps and improperly disposing of devices. Data encryption and authentication mechanisms can protect patient information in case of user mistakes.
Role-based access control and the principle of least privilege (PoLP) ensure team members access only the data necessary for their roles. Applying these practices minimizes the risk of personnel-related mistakes during development and operations.
IoT devices increase the chances of noncompliance
Implementing IoT in telemedicine and other types of remote healthcare complicates regulatory compliance. Organizations must ensure secure storage, sharing, and disposal of devices and the patient data they collect.
You must follow all data privacy laws, including industry-standard regulations, like HIPAA (US), GDPR (EU), UK-GDPR (UK), and CCPA (California). The US FDA also imposes requirements for managing IoT devices, related clinical support, and administrative healthcare data management software.
Embedding security practices into every part of a product’s lifecycle, including development and deployment, can address these problems. However, if these risks are ignored, companies can face several complications.
Business Impact of Poor IoT Security in Healthcare
Poor healthcare security can affect your company’s financial status and reputation. Here are the most probable consequences of security breaches and how good DevSecOps practices can reduce them.
Direct financial losses
IoT security breaches can lead to expensive remediation. You may need to assemble expensive resources to identify the source of a breach, and you may have to compensate affected patients. In addition, there may be fines if an investigation reveals that your negligence permitted the breach, and your customers may experience costly IoT service disruptions until fixes are implemented.
According to IBM’s 2022 Cost of a Data Breach Report, the average healthcare-related breach reached a new all-time high cost of $10.1 million in 2022. Across all industries, data breaches in the healthcare industry have been the most expensive for twelve years straight. Notably, 24% of these costs were accrued two years after an initial breach, indicating that the costs continue to build long after an incident.

DevSecOps teams can proactively identify bugs and security issues in IoT devices and related software before they become critical vulnerabilities. This can significantly reduce remediation costs and unexpected downtime.
Costs of legal action
Data breaches leak sensitive information that invites all types of fraud, including identity theft. Patients can sue for losses, and those lawsuits come with hefty legal fees and settlements. On top of that, if an investigation finds that your company did not comply with data security and privacy regulations, you may face financial penalties. For example, HIPAA violation fines range from $100 to $50,000 per violation, with a maximum of $1.5 million per calendar year.
Let’s look at a data breach suffered by Anthem Inc. that affected 78.8 million people (figures from the 2022 Healthcare Data Breach report). The incident cost Anthem $230 million: $115 million for lawsuits, $39.5 million for a settlement with the state, and $16 million for investigations by the US Department of Health and Human Services.
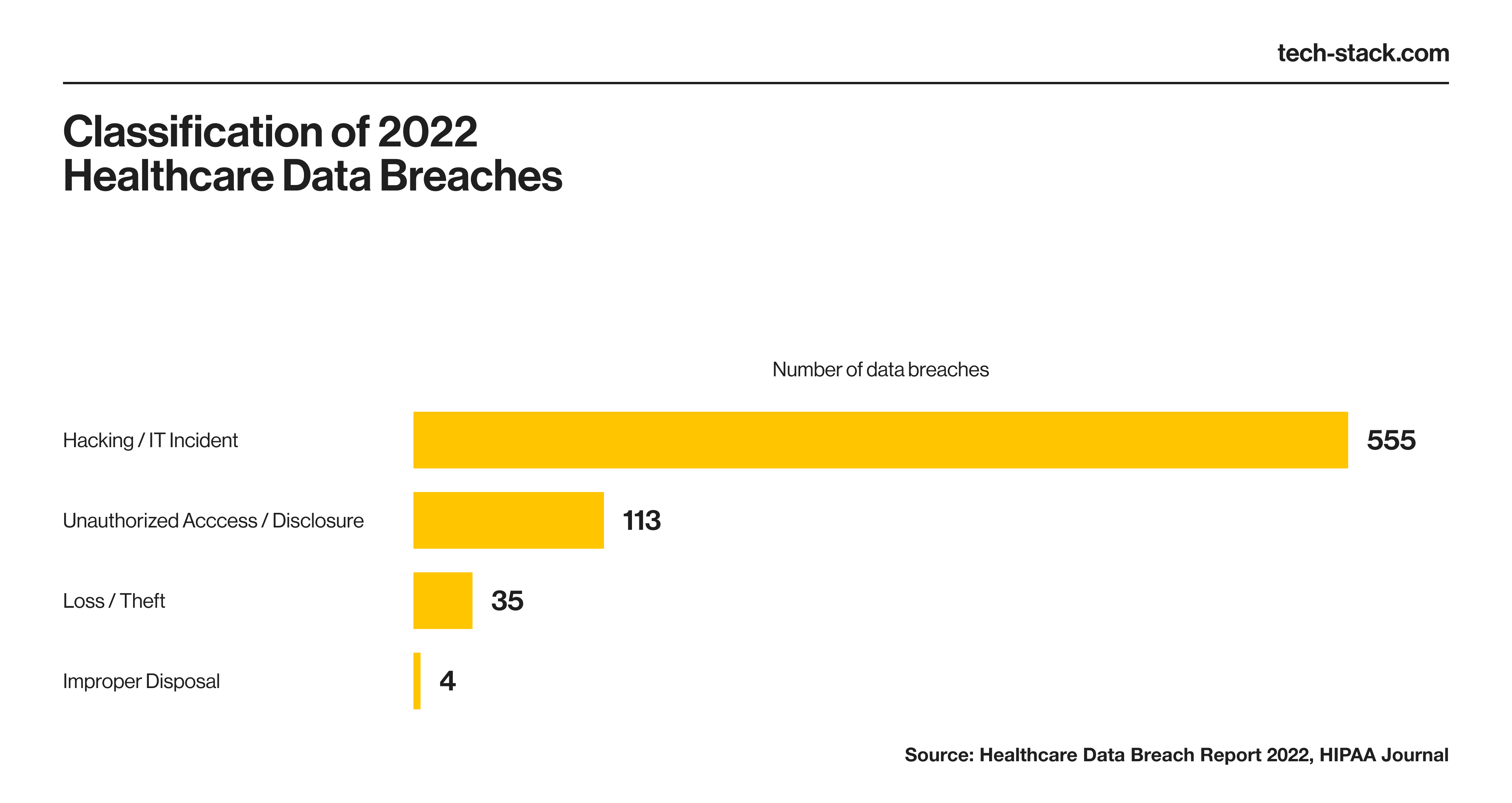
Integrating security tools and practices enhances the safety of your patient data, minimizing the risk of lawsuits and regulatory fines.
Lost business opportunities
Security incidents damage your reputation among healthcare providers, business associates, and patients, leading to lower patient retention and acquisition rates as well as lost opportunities with business associates.
Even minor incidents can prove costly. In 2021, Scripps Health suffered a ransomware attack that breached 1.2 million patient records. The company spent $21 million on remediation and lost $92 million worth of business opportunities.
Focusing on data protection during IoT implementation demonstrates your dedication to patient safety. This enhances your brand’s image, helps retain patients, and creates new business opportunities.
Development delays
Vulnerabilities identified late in the development process prolong the time-to-market. The closer a product is to deployment, the more time you need to fix bugs because they may iterate back to earlier stages in the code. Identifying their root causes frequently requires regression testing, defect analysis, and vulnerability assessments. These results in time-consuming delays and missed revenue opportunities.
Integrating security practices into the development lifecycle helps organizations improve their security posture and operational effectiveness by aligning development, operations, and security teams. In the hands of experienced management, this methodology brings highly reliable IoT products to market.
Now, let’s see how to add DevSecOps successfully to an established workflow.
DevSecOps in Healthcare IoT: Best Practices
In this section, we want to share best practices that your organization can use to bring DevSecOps methodology into your healthcare IoT development and operations process.
Implement consistent security policies
Healthcare organizations must create security standards for development, data sharing, and IoT device use. The goal is to ensure that all team members—from software engineers to medical staff and patients—understand their role in maintaining a secure environment. Key policies may include:
- RBAC. Role-based access control measures, like PoLP, ensure that users have clearance to access only resources required to execute their responsibilities.
- Zero trust. A security model that, by default, treats every IoT device and user in the network as a threat.
- Network segmentation. The IoT network and remote devices should be isolated from other parts of your IT infrastructure to contain the damage from breaches.
- Device monitoring. Robust authentication mechanisms and ongoing device monitoring allow your team to respond to security threats as soon as they’re detected.
- Incident response. Your IoT strategy should include proactive and reactionary measures that minimize disruptions in case of an unauthorized access attempt or other security incidents.
Another major point: According to a 2022 research report in the Information and Software Technology journal, the ability to communicate these standards to your DevOps team is one of the biggest challenges when implementing DevSecOps. However, shifting your developer’s focus to security makes development more actionable.
Maintain secure coding standards
Adhering to secure coding standards prevents vulnerabilities in IoT devices and systems. Your security specialists and quality assurance experts should establish criteria for approving and rejecting code. These standards can be specific to language constructs and specific technology stacks.
Code review should be frequent, organized, and objective. Your team should never skip over a piece of code that violates your standards just because they think it’s not exploitable. In addition, programmers should document all errors throughout the development process.
Your team should also incorporate authentication measures for handling cloud APIs. Make sure they use approved cryptography methods to safeguard data at rest and in transit. It’s also vital to validate and sanitize input to ensure data conforms to the correct format without unwanted characters.
Prioritize high-risk areas with threat modeling
Threat modeling is the systematic process of identifying ways to attack your system. DevSecOps can use this during healthcare IoT development to pinpoint and prioritize high-risk areas.
The team should analyze each potential threat based on factors like the attack vector, threat source, likelihood of occurrence, and potential impact. They can then focus their efforts on the most critical risks.
Incorporating threat modeling into DevOps lets your team anticipate vulnerabilities. They can then devise appropriate mitigation strategies for each threat type, yielding a more secure IoT product.
Invest in automated DevSecOps tools
Many security problems in DevSecOps result from a lack of automated testing tools. That’s why it pays to invest in automated security scans, code verifications, and dependency checks. Moreover, integrating these tools into your CI/CD pipeline can ensure that static tests are consistently conducted throughout the development cycle of an IoT healthcare product.
Adopting black-box security testing tools can enhance quality assurance assessments. Such tools simulate various threats to identify vulnerabilities from an external perspective (without knowledge of your internal structure and design). This extra security layer prevents issues from slipping by regular static analysis and code reviews.
Measure DevSecOps performance
Performance indicators help you measure how security impacts your development process. Focus on relevant performance indicators that gauge your team’s productivity, process bottlenecks, and system reliability.
Established DevOps metrics can serve as a basis to determine the key performance indicators for security. The core KPIs include:
- Mean time to recovery—how fast your development team fixes the system after failures to continue their operations
- Time to restore service:how long it takes to restore IoT service after interruptions that impact users
- Change failure rate:the percentage of code that leads to failure in production and requires security patches, hotfixes, or other remediation
- Deployment frequency:how often your team releases secure code to production
Avoid tracking indicators that don't contribute to your security posture, such as the number of code commits or detected raw bug counts. Focusing on irrelevant metrics can even hurt your productivity.
You should regularly review your DevSecOps processes. Keeping pace with the latest tools and practices help you to constantly improve the security of any IoT technologies you introduce, improve your brand’s reputation, and expand your client base.
Tackling Concerns About Adopting DevSecOps in Healthcare
It’s natural to have some concerns when shifting left. This section addresses them so you’ll feel confident about implementing security practices into the development.
Resistance to change
Resistance is natural during transformational changes. Employees might oppose the shift if the goals are not clearly communicated or come from the top down without explanation. If the team resists the change, they will not make an effort to master DevSecOps tools.
We recommend transparency—help your team understand the benefits of implementing new practices. Involve them in decisions and consider their suggestions so they know you value their input about the transformation. To help your team adapt, arrange workshops and individual training on the latest tools.
Cultural and organizational mindset
Development, operations, and security departments historically worked in silos. In other words, they worked alone and collaborated only when absolutely necessary (like after finding a critical bug). This meant limited visibility from the security department into the development department, and the DevOps team didn’t prioritize security when implementing IoT in healthcare.
According to Accelerate’s 2022 State of DevOps report, cultural aspects were the biggest predictor of the security practice effectiveness. High-trust and low-blame environments (where employees trust one another and don’t fear taking responsibility for their actions) are 1.6 times more likely to adopt DevSecOps successfully.
So, it’s your job to break down the silos by promoting trust and open communication. Value-driven performance metrics (as previously described) also help teams align their efforts and create a sense of shared responsibility.
Resource and time constraints
DevSecOps requires a lot of resources to conduct all the different types of security checks that must happen before a product launch. This includes investment in hiring, training, and retaining security specialists. Less experienced teams might achieve high IoT security, but at the cost of overworking and burning out professionals.
Start implementing DevSecOps gradually instead of attempting to reorganize the entire development process in one fell swoop. Your teams will adapt if you begin with the most critical security threats. Additionally, automated tools reduce the manual workload for DevSecOps and other teams.
Scarcity of security specialists
The SANS 2022 DevSecOps Survey revealed that 44.1% of respondents said a shortage of application security skills (up from 37.8% in 2021) was one of the biggest barriers to implementing DevSecOps practices. The scarcity of cloud security personnel was a barrier for 25.1% of respondents, and a lack of coding skills in security teams was cited by 22.9% of respondents.

Companies can explore emerging and underutilized DevSecOps tools to cope with these personnel challenges. For example, AI/ML-powered scans, application security orchestration and correlation (ASOC), and cloud security posture management (CSPM) tools can streamline your security profile.
Your organization can also seek partnerships with software development companies that shift left during DevOps. This approach offers the expertise of seasoned experts as you upskill your in-house employees.
Final Thoughts
IoT in healthcare can enhance patient monitoring and effective telehealth technology to improve patient outcomes. However, IoT implementation increases the risk of data and privacy breaches and regulatory noncompliance.
You can address these challenges by implementing DevSecOps in healthcare technology development and IT operations. A shift-left security approach reduces the likelihood that IoT devices and applications will be exploited because it emphasizes security at the earliest stages of the development life cycle. This methodology also makes the development process more efficient and reduces long-term costs if correctly implemented.
Do you need help navigating DevSecOps challenges? Our security and DevOps services can tackle your needs and ensure your IoT infrastructure and product development follow the strictest healthcare security requirements.






